Foreman openidc SSO with keycloak

I this post I will show you how you can configure Foreman to use Keycloak asz an OIDC SSO authentication provider.
I use a Self-signed certificate for keycloak so my first step is to add the root CA of this certificate as a trusted certificate on the foreman server:
cp rootca.crt /etc/pki/ca-trust/source/anchors/
update-ca-trust
install requirements
yum install mod_auth_openidc keycloak-httpd-client-install
The keycloak-httpd-client-install is a commandline tool thet helps to configure the apache2’s mod_auth_openidc plugin with Keycloak. This feature is not yet supported by foreman-installer. As a result, re-running the foreman-installer command can purge the changes in Apache files added by the keycloak-httpd-client-install.
keycloak-httpd-client-install \
--app-name foreman-openidc \
--keycloak-server-url "https://keycloak.mydomain.intra" \
--keycloak-admin-usernam "admin" \
--keycloak-realm "ssl-realm" \
--keycloak-admin-realm master \
--keycloak-auth-role root-admin \
-t openidc -l /users/extlogin
systemct restart httpd
Configure Keycloak
We need to create two mappers for the new client in keycloak:
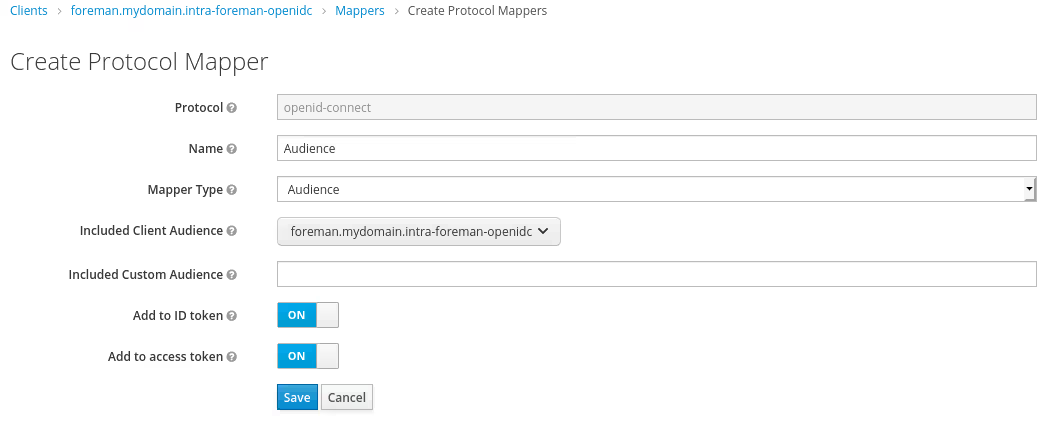
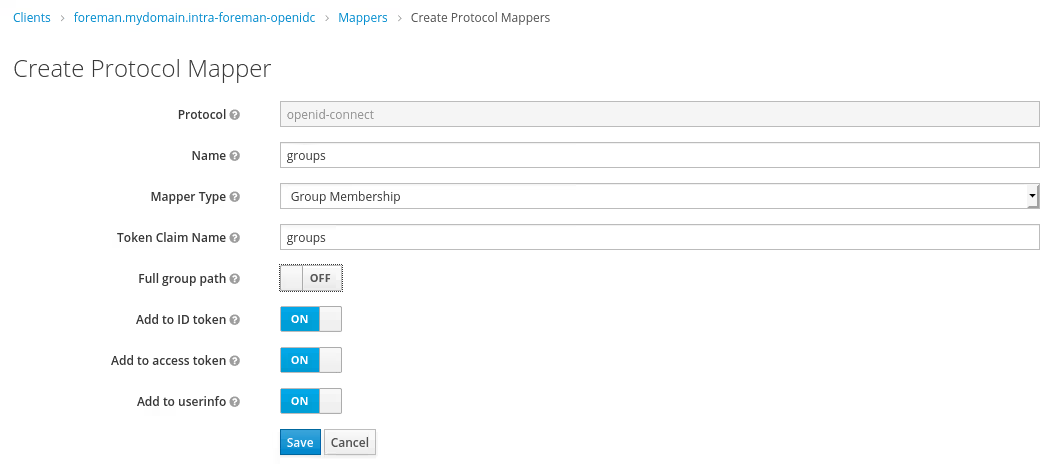
Then in Keycloak create a group called foreman-admin and add the test user for it.
Configure Foreman:
Administer / Settings / Authentication
Authorize login delegation = yes
Authorize login delegation auth source user autocreate = External
OIDC Algorithm = RS256
# the client id from keycloak
OIDC Audience = foreman.mydomain.intra-foreman-openidc
OIDC Issuer = https://keycloak.mydomain.intra/auth/realms/ssl-realm
OIDC JWKs URL = https://keycloak.mydomain.intra/auth/realms/ssl-realm/protocol/openid-connect/certs
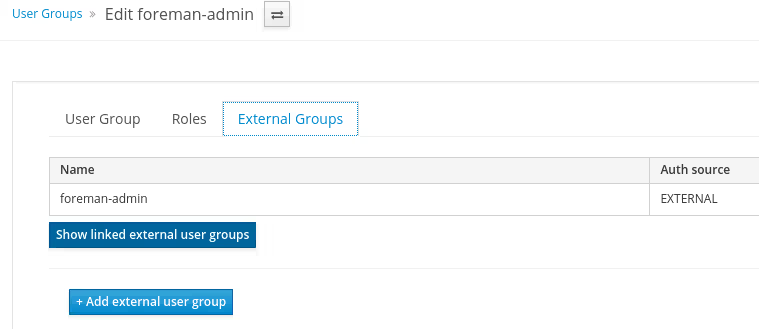
Create an user groupe in foreman called foreman-admin and map with the external group called foreman-admin.
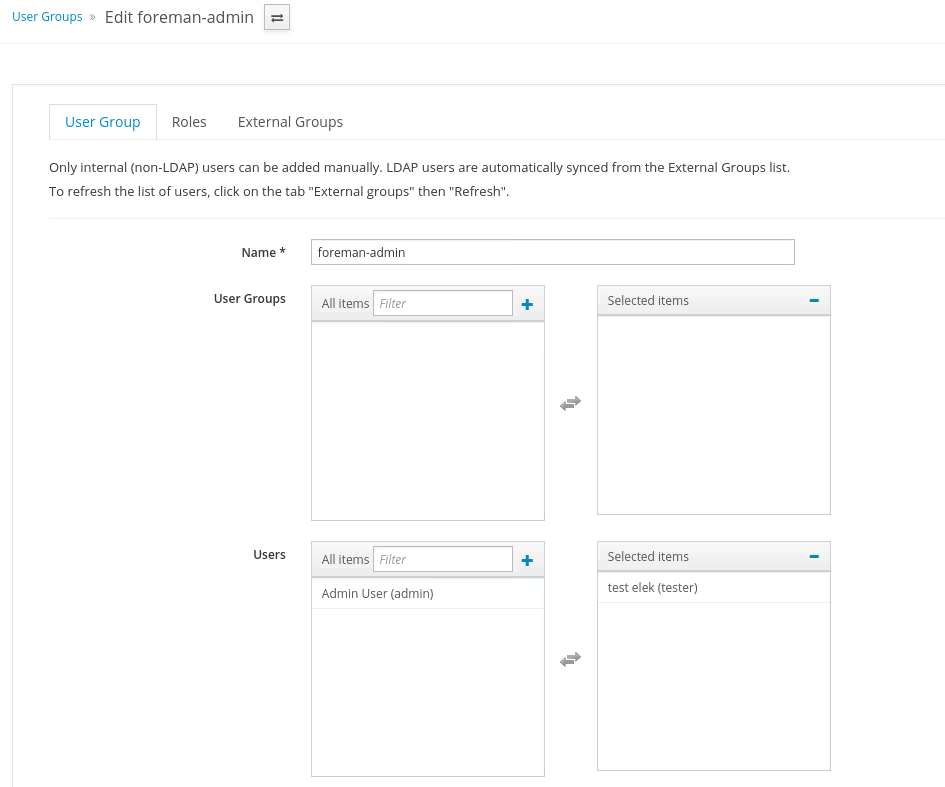
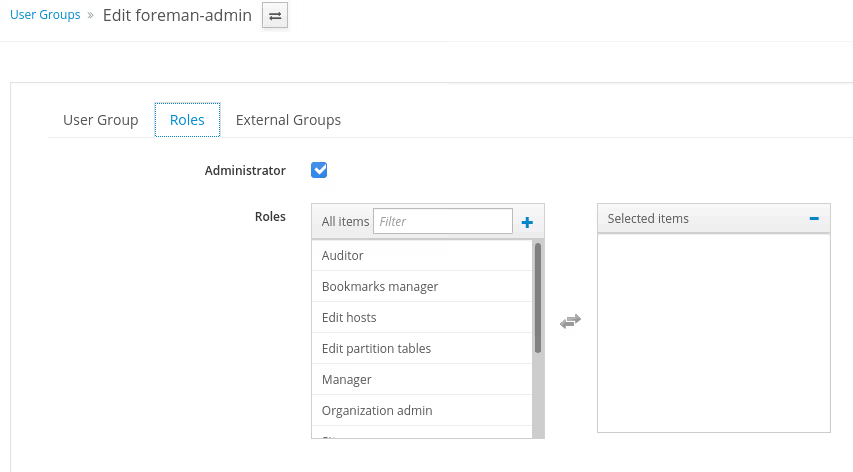
The log out and go the he url of the foreman. It will redirect to Keycloak to login. Add the test users credentials the login wit it.

