Firewall Ports for AD Domain Join
Page content
In this post I will show you what port you need to enable for AD Domain Join.
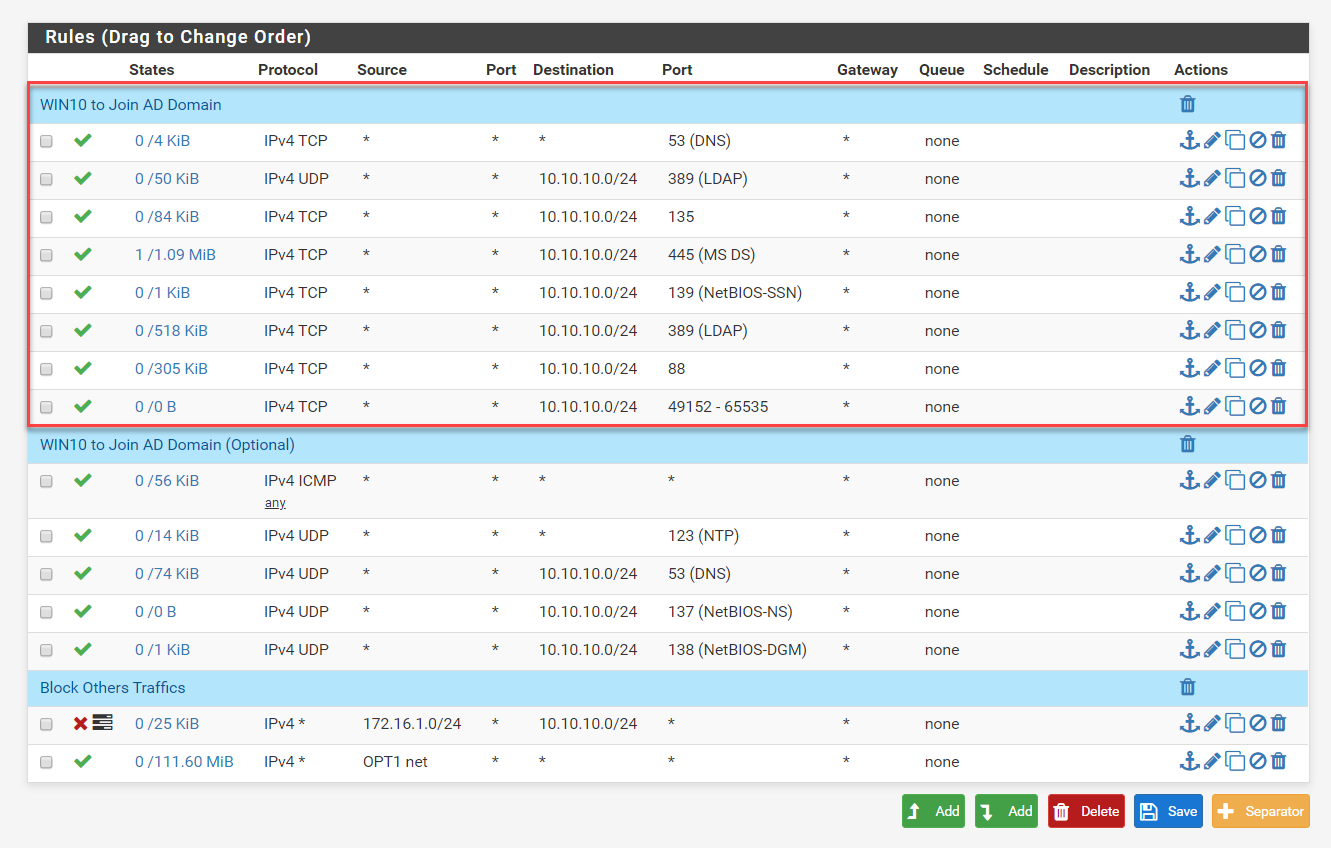
Firewall Ports required to join AD Domain (Minimum)
Windows 10 Client can join to Windows 2019 AD Domain with the following Ports allow in Firewall
- TCP 88 (Kerberos Key Distribution Center)
- TCP 135 (Remote Procedure Call)
- TCP 139 (NetBIOS Session Service)
- TCP 389 (LDAP)
- TCP 445 (SMB,Net Logon)
- UDP 53 (DNS)
- UDP 389 (LDAP, DC Locator, Net Logon)
- TCP 49152-65535 (Randomly allocated high TCP ports)
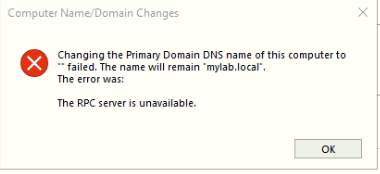
Without TCP High Ports open the following Message appear even join to domain successfully:
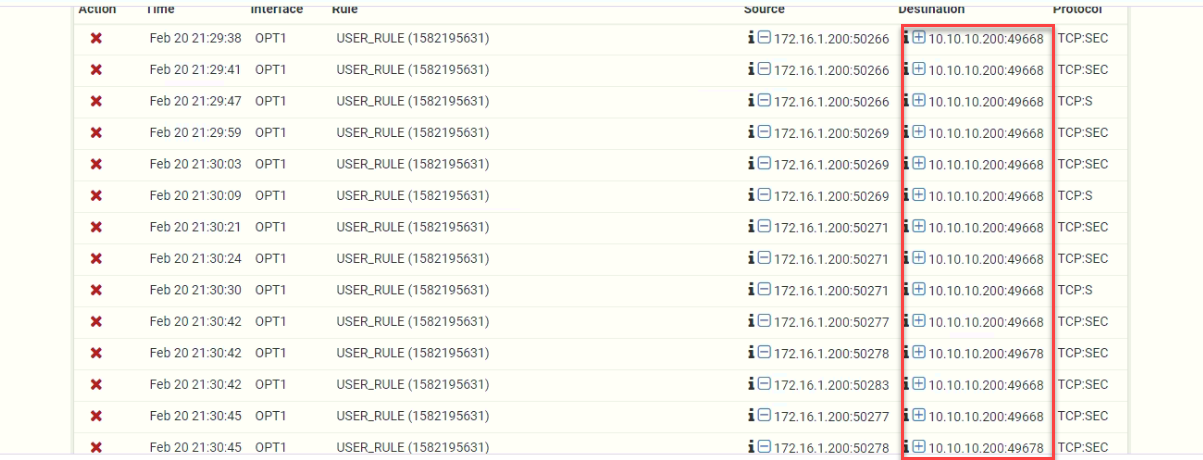
there is a lot of TCP high ports are blocked in Firewall:
Optional Ports
- UDP 123 (NTP)
- TCP 53 (DNS)
- TCP 464 ( Kerberos Password V5 – Used when user change their password from desktop)
- UDP 137 (NetBIOS Name Resolution)
- UDP 138 (NetBIOS Datagram Service)
- TCP 636 (LDAP SSL)
- UDP 636 (LDAP SSL)
- TCP 3268 (Global Catalog)
User can still change their password successfully even thought TCP 464 is blocked in Firewall
Firewall Rules in pfesense Firewall