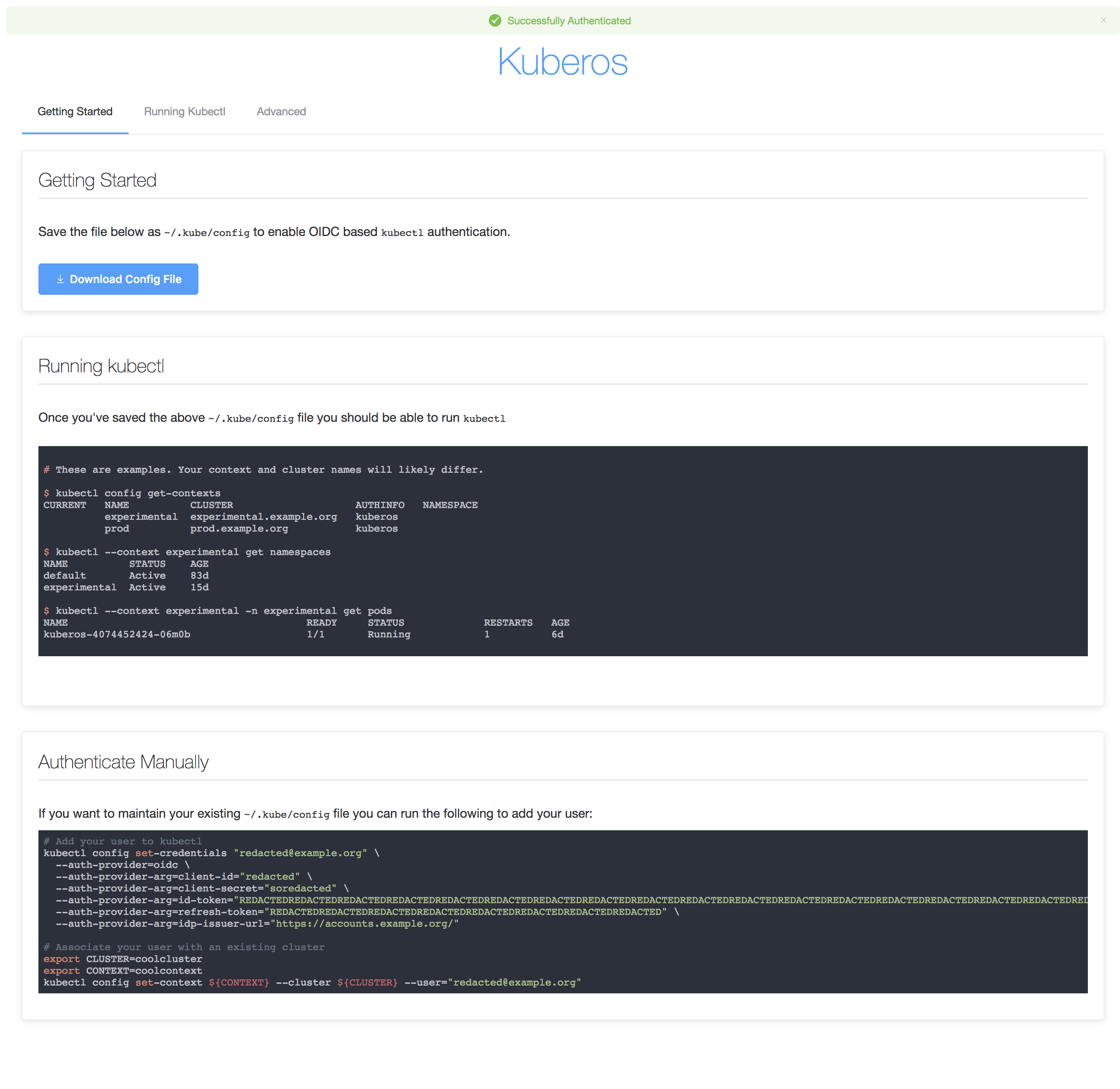
Kubectl authentication with Kuberos
Kuberos is an OIDC authentication helper for kubectl login.
Kuberos hase bean dpricated at May 10, 2019.
Parts of the Kubernetes series
- Part1a: Install K8S with ansible
- Part1b: Install K8S with kubeadm
- Part1c: Install K8S with kubeadm and containerd
- Part1d: Install K8S with kubeadm and allow swap
- Part1e: Install K8S with kubeadm in HA mode
- Part2: Intall metal-lb with K8S
- Part2: Intall metal-lb with BGP
- Part3: Install Nginx ingress to K8S
- Part4: Install cert-manager to K8S
- Part5a: Use local persisten volume with K8S
- Part5b: Use ceph persisten volume with K8S
- Part5c: Use ceph CSI persisten volume with K8S
- Part5d: Kubernetes CephFS volume with CSI driver
- Part5e: Use Project Longhorn as persisten volume with K8S
- Part5f: Use OpenEBS as persisten volume with K8S
- Part5f: vSphere persistent storage for K8S
- Part6: Kubernetes volume expansion with Ceph RBD CSI driver
- Part7a: Install k8s with IPVS mode
- Part7b: Install k8s with IPVS mode
- Part8: Use Helm with K8S
- Part9: Tillerless helm2 install
- Part10: Kubernetes Dashboard SSO
- Part11: Kuberos for K8S
- Part12: Gangway for K8S
- Part13a: Velero Backup for K8S
- Part13b: How to Backup Kubernetes to git?
- Part14a: K8S Logging And Monitoring
- Part14b: Install Grafana Loki with Helm3
nano /etc/kubernetes/manifests/kube-apiserver.yaml
...
command:
- /hyperkube
- apiserver
- --advertise-address=10.10.40.30
...
- --oidc-issuer-url=https://keycloak.devopstales.intra/auth/realms/mydomain
- --oidc-client-id=k8s
- --oidc-username-claim=email
- --oidc-groups-claim=groups
...
systemctl restart docker kubelet
cat <<'EOF'> values.yaml
replicaCount: 1
kuberos:
oidcClientURL: https://keycloak.devopstales.intra/auth/realms/mydomain
oidcClientID: k8s
oidcSecret: 43219919-0904-4338-bc0f-c986e1891a7a
clusters:
- name: openshift
apiServer: https://192.168.0.106:6443
# `apiServer` is the url for kubectl
# This is typically https://api.fqdn
caCrt: |-
-----BEGIN CERTIFICATE-----
MIIDZDCCAkygAwIBAgIIe/R9sc8oJiAwDQYJKoZIhvcNAQELBQAwFTETMBEGA1UE
AxMKa3ViZXJuZXRlczAeFw0xOTEyMjcxNzM3MzlaFw0yMDEyMjYxNzM3MzlaMBkx
FzAVBgNVBAMTDmt1YmUtYXBpc2VydmVyMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8A
MIIBCgKCAQEAzAg7MflA/HVTVcZPsGJH71cfcJ/U1CtEYbXfu/AQbhGg09XKmeK9
aGEK3kSgi/Hyoi7M+e/ntx1+Gp/jwc8kanMFRLgxdKCxxi4MOswZF/q2loUdNoE/
OQVPWQi8Hgznubw/0gINUkIq8mRx9Bb+RcRnJEfD3CXkxDhUNeCvvjeTrujguF0h
pgfzrLoc2kGdJYpHiLqow8jRq7XXk0RzZaqCQjAEZgqWamwbTTqFZh3v+1gF/2s0
EbFVVL2Ctu1dOGe1FkZxte7/Po1XBkPLQuRXbH3QRiJkPfyOW16T1nWk1QTcpCdH
HO/l+CY2nLPFZL1BM83QuVmPgR1T1p+5tQIDAQABo4GzMIGwMA4GA1UdDwEB/wQE
AwIFoDATBgNVHSUEDDAKBggrBgEFBQcDATCBiAYDVR0RBIGAMH6CEms4cy5teWRv
bWFpbi5pbnRyYYIKa3ViZXJuZXRlc4ISa3ViZXJuZXRlcy5kZWZhdWx0ghZrdWJl
cm5ldGVzLmRlZmF1bHQuc3ZjgiRrdWJlcm5ldGVzLmRlZmF1bHQuc3ZjLmNsdXN0
ZXIubG9jYWyHBApgAAGHBMCoAGowDQYJKoZIhvcNAQELBQADggEBAJZ7jxPR72V6
PYL3SKCWaS+RgTuGuSm0pYu26cBmPOjsugd8DUrJ7+iAnKDHUmmw22sWheLLCokc
YU/AIfdbbsz0+f+/qthkO7zJmAJgdIAOMJ5MQCbxMBt+6L813r1R3QI7kAGxHvzV
loKJVIIHq/6K3gFEZDfo0myvNvtOIpBCeMnZRK+8hx3UNcHckZbhkan1Z1j9t9iw
b6Vv5jY1+9t2Iltd2wuNaUvHicx+3X6JPAqVR6H0jI3i+QSyT1EHXtBtbQBBpP4T
5WDz+9uDa1mIDHtww7DTnJwY+hGI7fVF2H7XQaM4xwhGnwIwbkSh45JWVtUEHMou
Q7T4bTyrwuQ=
-----END CERTIFICATE-----
# `caCrt` is the public / CA cert for the cluster
# cat /etc/kubernetes/pki/apiserver.crt
ingress:
enabled: true
annotations:
kubernetes.io/ingress.class: nginx
nginx.ingress.kubernetes.io/proxy-buffer-size: "64k"
cert-manager.io/cluster-issuer: ca-issuer
ingress.kubernetes.io/force-ssl-redirect: "true"
path: /
hosts:
- kubectl.devopstales.intra
tls:
- secretName: default-cert
hosts:
- kubectl.devopstales.intra
image:
repository: negz/kuberos
tag: ede4085
pullPolicy: IfNotPresent
service:
type: ClusterIP
port: 80
annotations: {}
# Add your service annotations here.
resources: {}
EOF
helm repo add devopstales https://devopstales.github.io/helm-charts
helm upgrade --install kuberos devopstales/kuberos --namespace kuberos -f values.yaml
Below is an example of a ClusterRoleBinding that binds the role cluster-admin to the Keycloak group devops-team. (In my case it came from ldap) Create your own role bindings to fit your needs and apply them to the cluster.
nano devops-team_ClusterRoleBinding.yaml
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: cluster-admin-it-afdeling
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-admin
subjects:
- apiGroup: rbac.authorization.k8s.io
kind: Group
name: devops-team
nano user_ClusterRoleBinding.yaml
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: devopstales-admin
subjects:
- kind: User
apiGroup: rbac.authorization.k8s.io
name: devopstales
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-admin