Continuous Image Security
In this post I will show you my tool to Continuously scann deployed images in your Kubernetes cluster.
Parts of the K8S Security Lab series
Container Runetime Security
- Part1: How to deploy CRI-O with Firecracker?
- Part2: How to deploy CRI-O with gVisor?
- Part3: How to deploy containerd with Firecracker?
- Part4: How to deploy containerd with gVisor?
- Part5: How to deploy containerd with kata containers?
Advanced Kernel Security
- Part1: Hardening Kubernetes with seccomp
- Part2: Linux user namespace management wit CRI-O in Kubernetes
- Part3: Hardening Kubernetes with seccomp
Network Security
- Part1: RKE2 Install With Calico
- Part2: RKE2 Install With Cilium
- Part3: CNI-Genie: network separation with multiple CNI
- Part3: Configurre network wit nmstate operator
- Part3: Kubernetes Network Policy
- Part4: Kubernetes with external Ingress Controller with vxlan
- Part4: Kubernetes with external Ingress Controller with bgp
- Part4: Central authentication with oauth2-proxy
- Part5: Secure your applications with Pomerium Ingress Controller
- Part6: CrowdSec Intrusion Detection System (IDS) for Kubernetes
- Part7: Kubernetes audit logs and Falco
Secure Kubernetes Install
- Part1: Best Practices to keeping Kubernetes Clusters Secure
- Part2: Kubernetes Secure Install
- Part3: Kubernetes Hardening Guide with CIS 1.6 Benchmark
- Part4: Kubernetes Certificate Rotation
User Security
- Part1: How to create kubeconfig?
- Part2: How to create Users in Kubernetes the right way?
- Part3: Kubernetes Single Sign-on with Pinniped OpenID Connect
- Part4: Kubectl authentication with Kuberos Depricated !!
- Part5: Kubernetes authentication with Keycloak and gangway Depricated !!
- Part6: kube-openid-connect 1.0 Depricated !!
Image Security
Pod Security
- Part1: Using Admission Controllers
- Part2: RKE2 Pod Security Policy
- Part3: Kubernetes Pod Security Admission
- Part4: Kubernetes: How to migrate Pod Security Policy to Pod Security Admission?
- Part5: Pod Security Standards using Kyverno
- Part6: Kubernetes Cluster Policy with Kyverno
Secret Security
- Part1: Kubernetes and Vault integration
- Part2: Kubernetes External Vault integration
- Part3: ArgoCD and kubeseal to encript secrets
- Part4: Flux2 and kubeseal to encrypt secrets
- Part5: Flux2 and Mozilla SOPS to encrypt secrets
Monitoring and Observability
- Part6: K8S Logging And Monitoring
- Part7: Install Grafana Loki with Helm3
Backup
In a previous posts we talked about admission-controllers that scnas the image at deploy. Like Banzaicloud’s anchore-image-validator and Anchore’s own admission-controller. But what if you run your image for a long time. Last weak I realised I run containers wit imagest older the a year. I this time period many new vulnerability came up.
I find a tool called trivy-scanner that do almast what I want. It scans the docker images in all namespaces with the label trivy=true and get the resoults to a prometheus endpoint. It based on Shell Operator that runs a small python script. I made my own version from it:
Deploy the app
git clone https://github.com/devopstales/trivy-scanner
nano trivy-scanner/deploy/kubernetes/kustomization.yaml
namespace: trivy-scanner
...
kubectl create ns trivy-scanner
kubectl aplly -k trivy-scanner/deploy/kubernetes/
Demo
Test the guestbook-demo namespace:
kubectl label namespaces guestbook-demo trivy=true
kubectl get service -n trivy-scanner
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
trivy-scanner ClusterIP 10.43.179.39 <none> 9115/TCP 15m
curl -s http://10.43.179.39:9115/metrics | grep so_vulnerabilities
Now you need to add the trivy-scanner Service as target for your prometheus. I created a ServiceMonitor object for that:
apiVersion: monitoring.coreos.com/v1
kind: ServiceMonitor
metadata:
labels:
serviceapp: trivy-exporter-servicemonitor
release: prometheus
name: trivy-exporter-servicemonitor
spec:
selector:
matchLabels:
app: trivy-scanner
endpoints:
- port: metrics
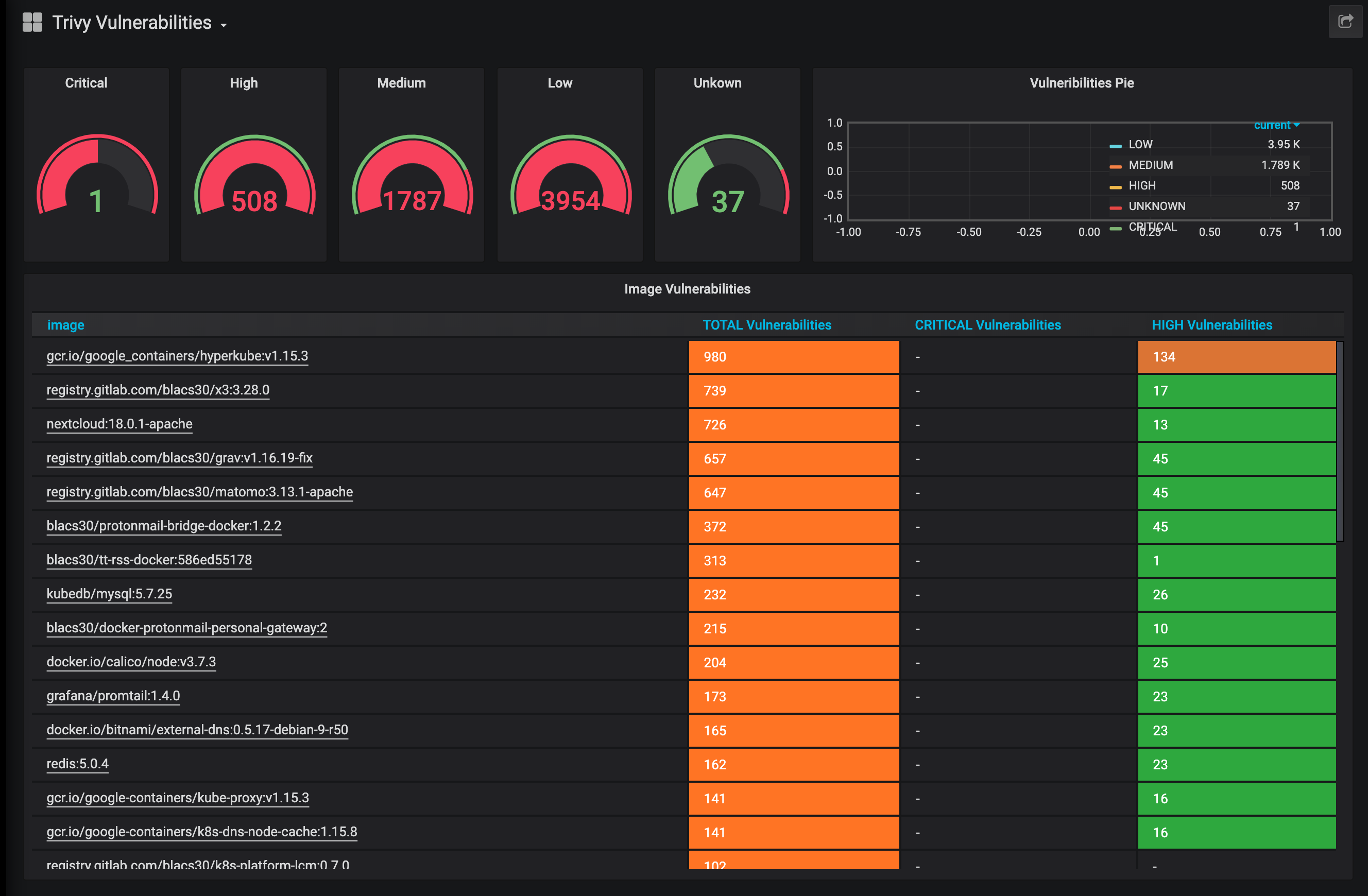
If you use my grafana dasgboard from the repo you can see someting like this: